Hello,
I have a report from Malwarebytes Premium that mudflow.exe was a Trojan using the Port of 10007 to connect to the IP 125.212.218.98, when I searched for this IP, it’s actually one of our ISP in Vietnam named as Viettel.
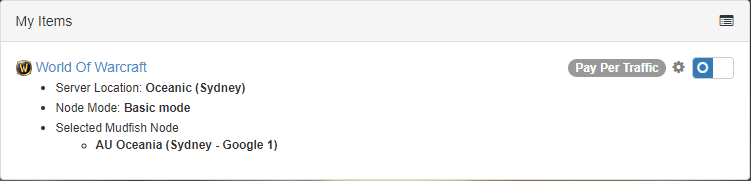
The thing is my connection was established to Google in Sydney for World of Warcraft (Oceanic), why does mudflow.exe tried to reach that specific IP domestically?
Thank you for your supports!
Corgei

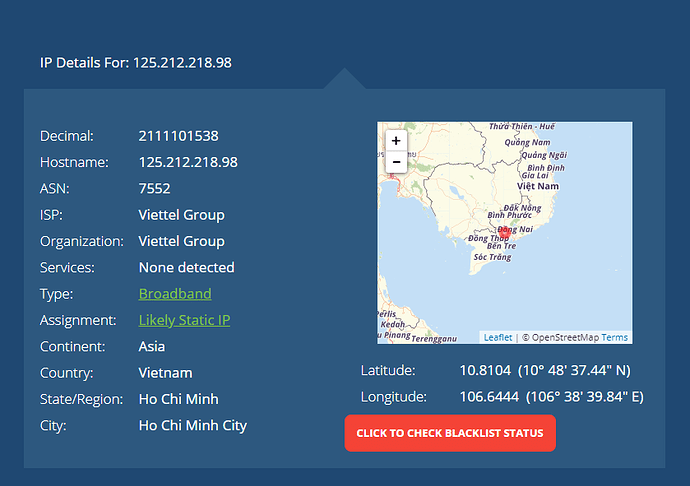
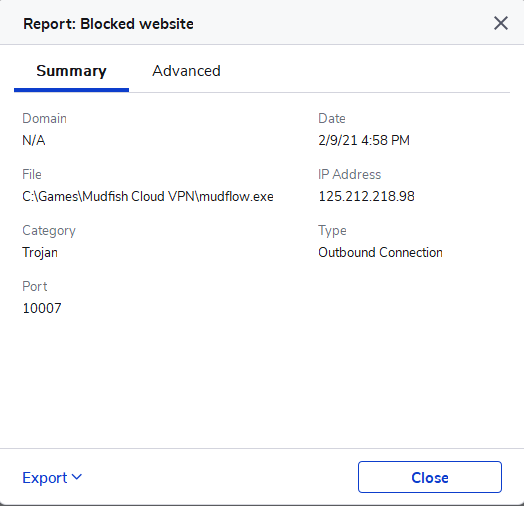
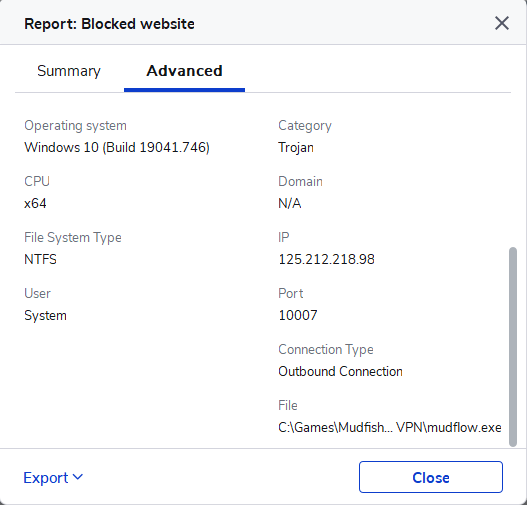
 Sorry for this inconvenience. 125.212.218.98 IP is a public IP of mudfish node “VN Asia (Vietnam - Viettel 2)” and TCP port 10007 is a echo daemon which is used to measure RTT between your desktop and mudfish nodes.
Sorry for this inconvenience. 125.212.218.98 IP is a public IP of mudfish node “VN Asia (Vietnam - Viettel 2)” and TCP port 10007 is a echo daemon which is used to measure RTT between your desktop and mudfish nodes. So at this moment no policy to detect whether the mudfish node is fully occupied or under heavy load. Only MRTG graphs are available in UI.
So at this moment no policy to detect whether the mudfish node is fully occupied or under heavy load. Only MRTG graphs are available in UI.